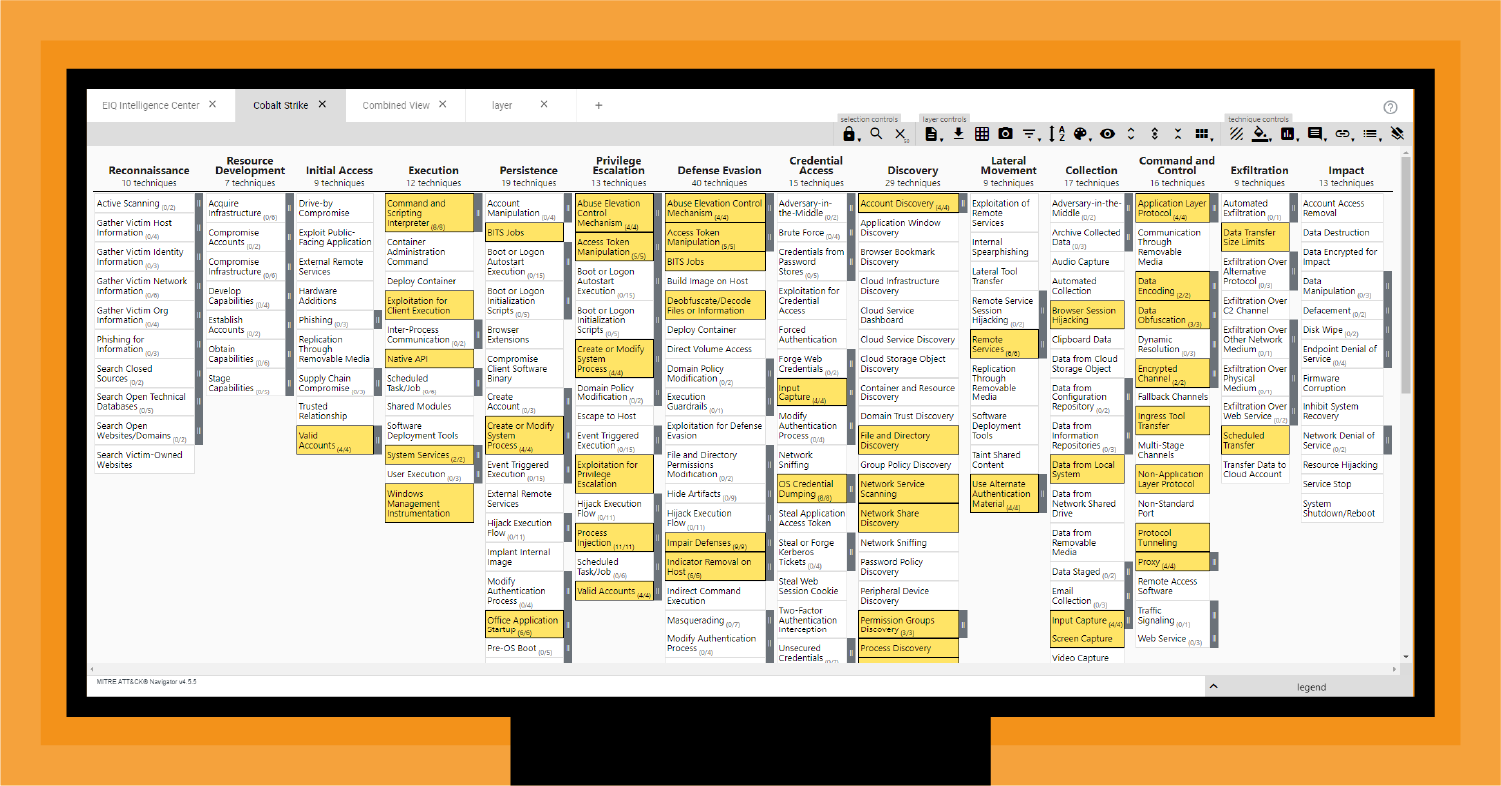
Mitre Att&Ck Mapping – Met 600 MDR-medewerkers wereldwijd kan Sophos die blinde vlek zichtbaar maken. Via samenwerkingen zoals met Veeam en Tenable kan Sophos die blinde vlek verkleinen. En, stelt Schippers tot slot als . A stealthy Linux malware named ‘sedexp’ has been evading detection since 2022 by using a persistence technique not yet included in the MITRE ATT&CK framework. .
Mitre Att&Ck Mapping
Source : www.microsoft.com
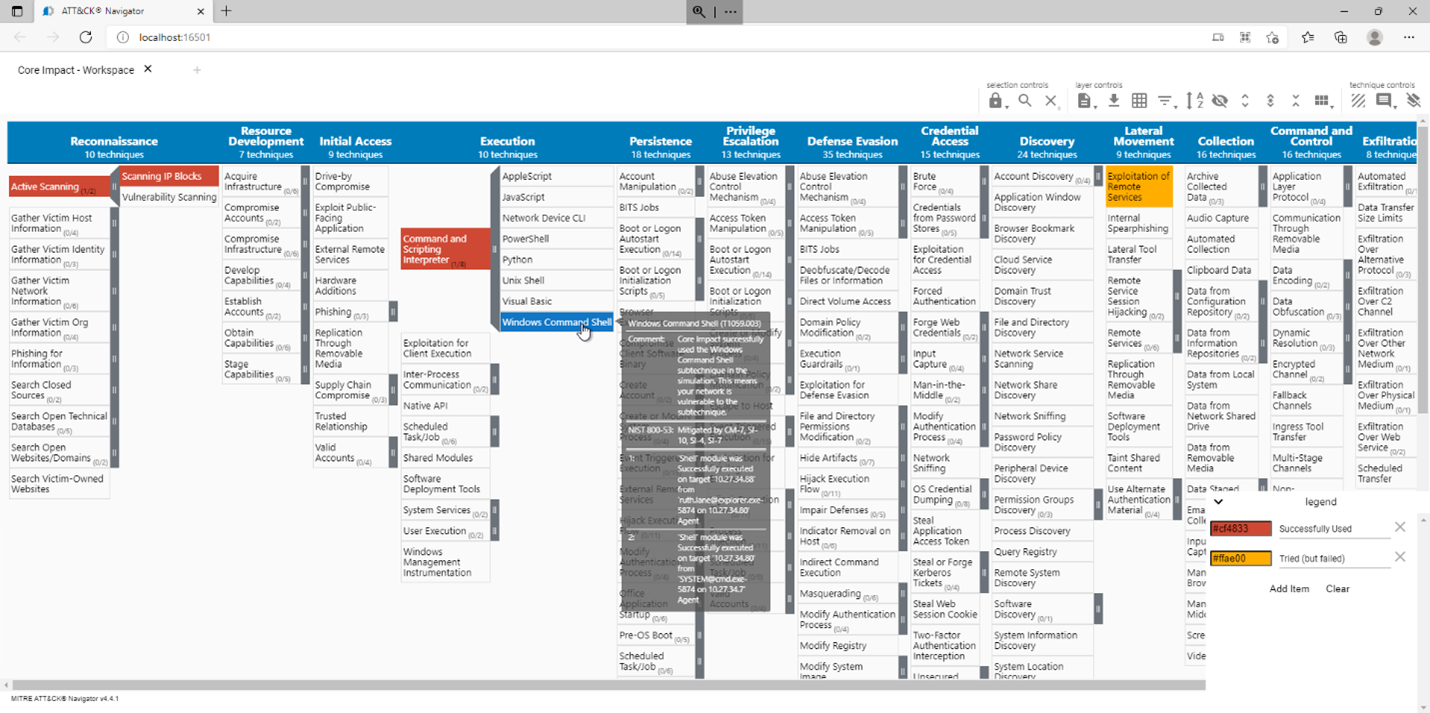
Core Impact 21.2: Incorporating the MITRE ATT&CK™ Framework and
Source : www.coresecurity.com
DeTT&CT: Mapping your Blue Team to MITRE ATT&CK™ — MB Secure
Source : www.mbsecure.nl
Assessing and expanding MITRE ATT&CK coverage in Splunk Enterprise
Source : lantern.splunk.com
DeTT&CT: Mapping your Blue Team to MITRE ATT&CK™ — MB Secure
Source : www.mbsecure.nl
NDR Contributions to MITRE ATT&CK Framework ExtraHop | ExtraHop
Source : www.extrahop.com
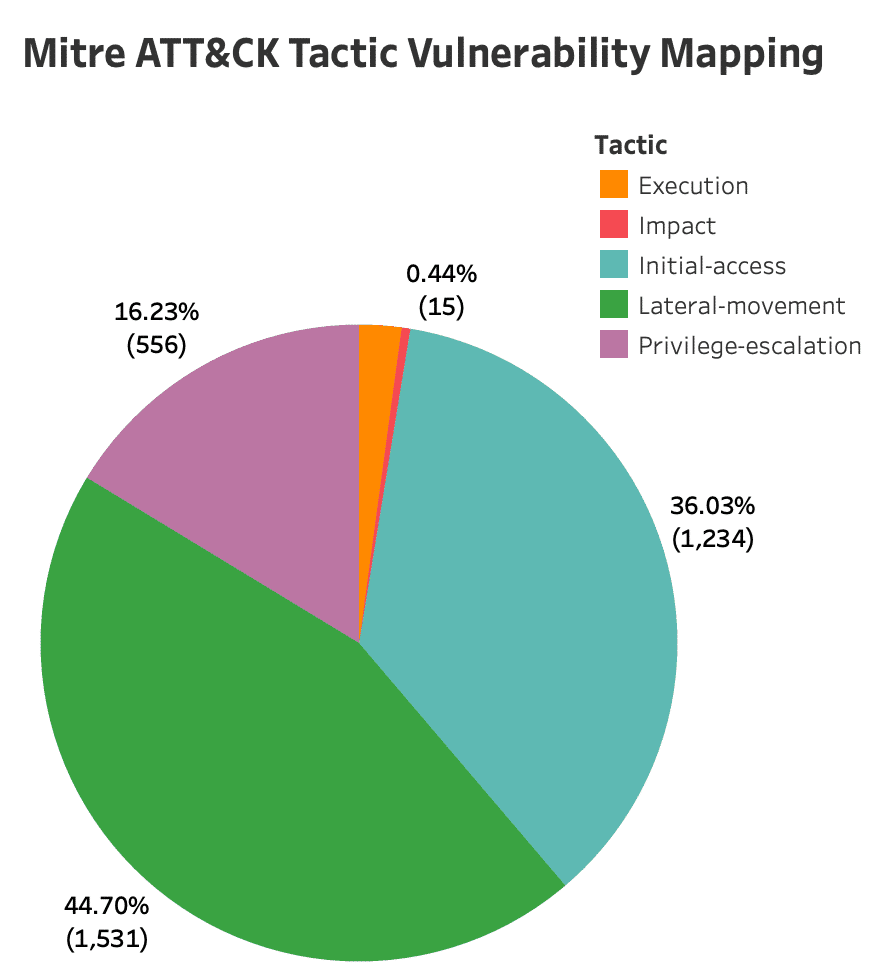
Top MITRE ATT&CK Tactics and Techniques Leveraged in 2023 | Qualys
Source : blog.qualys.com
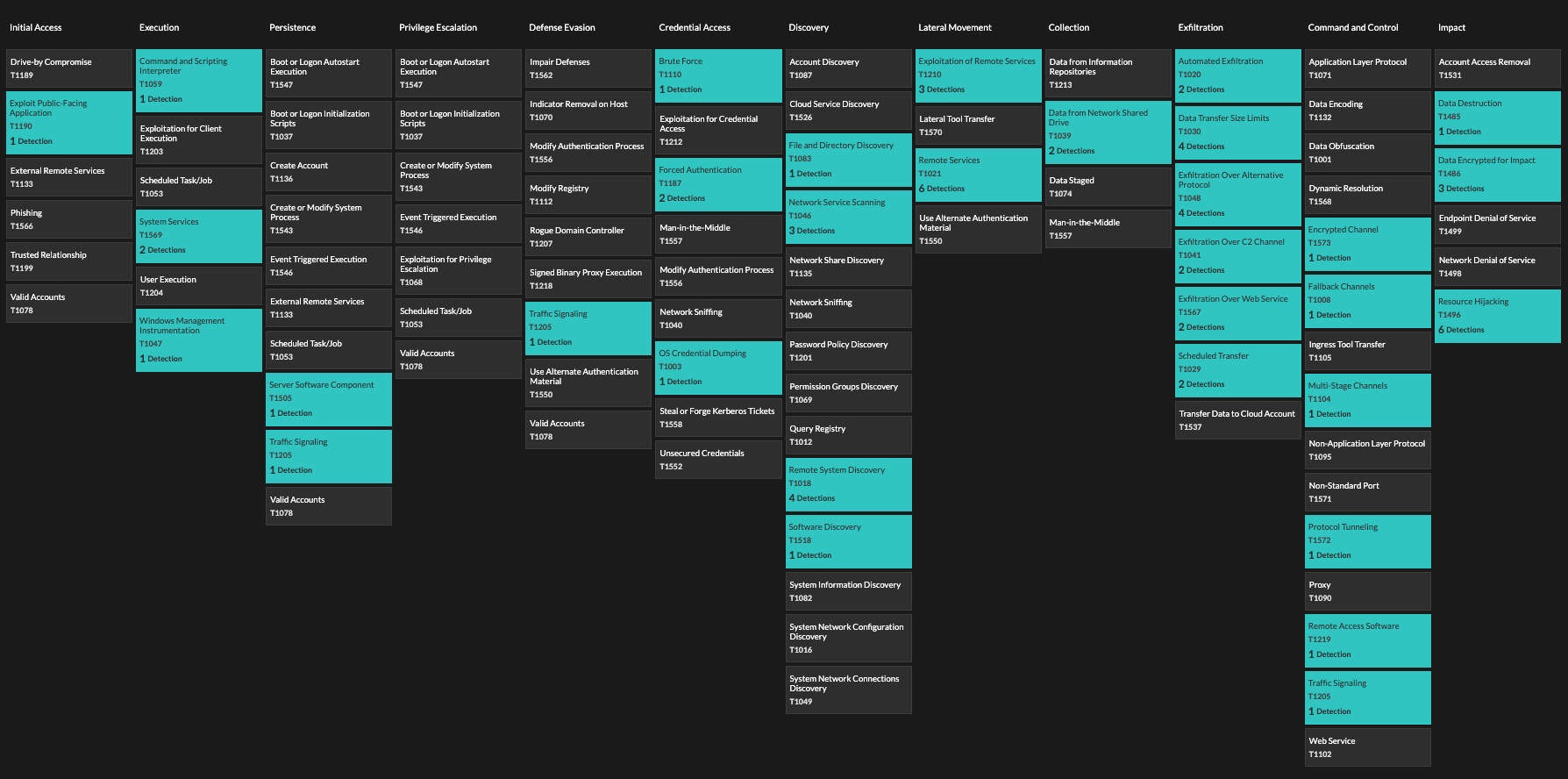
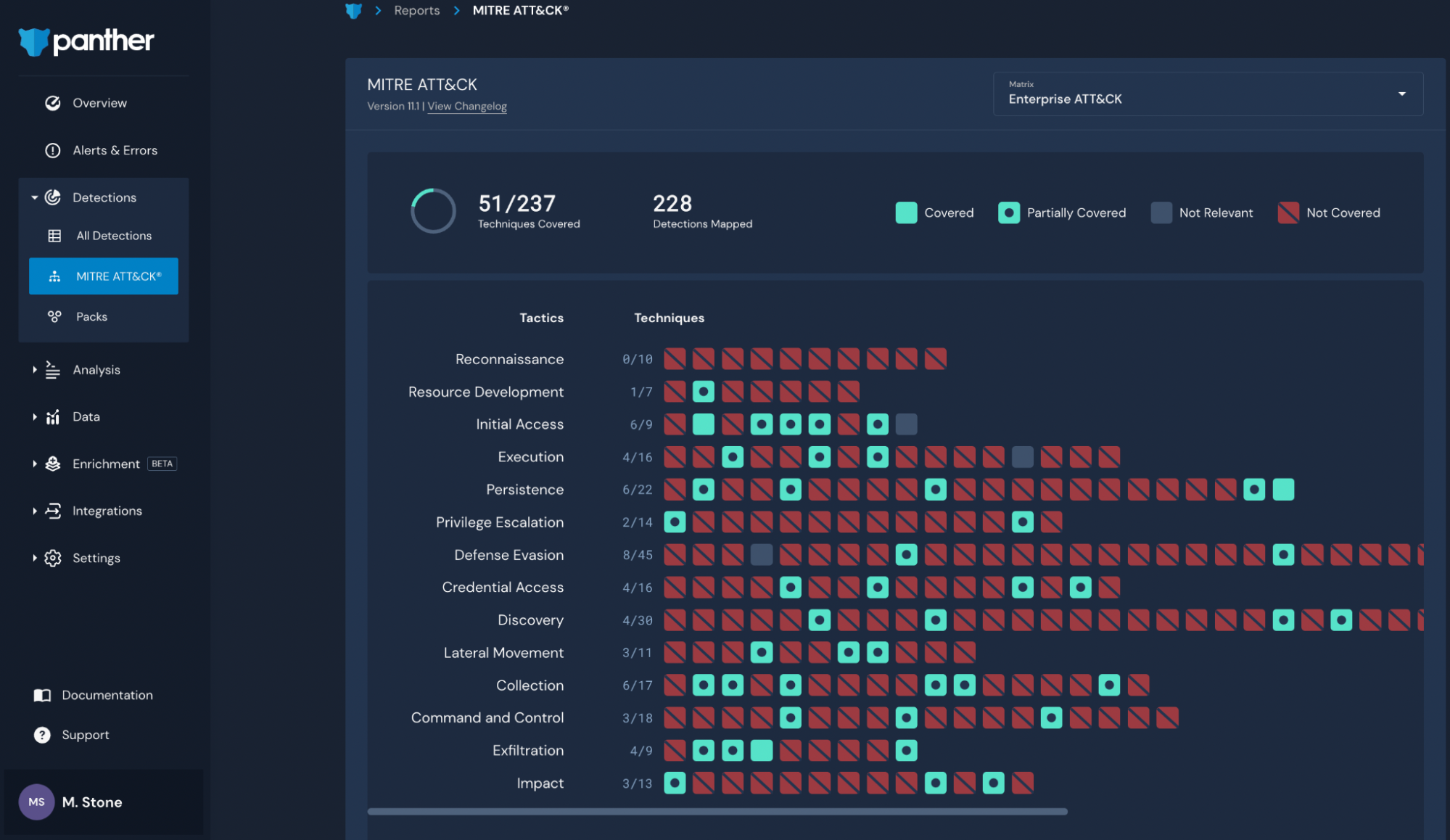
Using the MITRE ATT&CK Framework for Incident Response | Panther
Source : panther.com
How to Use MITRE ATT&CK to Map and Track Adversary TTPs | EclecticIQ
Source : www.eclecticiq.com
ATT&CK Data & Tools | MITRE ATT&CK®
Source : attack.mitre.org
Mitre Att&Ck Mapping MITRE ATT&CK® mappings released for built in Azure security : Security specialists recently discovered that the Linux malware variant “sedexp” evaded detection for two years by hiding in specific functions within the . The concept is well understood but putting it to work is much harder. Leading organizations provide some guidance on how to best implement this robust defensive strategy. .